Wyze March 2022 Exploit – Remote Clips and Images Access
In March 2022, we learned that Wyze cameras had a security exploit which allowed an attacker to gain access to the contents of the microSD card and view all stored video. This exploit was found in the Wyze Cam version 1, Wyze Cam Black version 2, as well as Wyze Cam version 3.
While the Wyze V2 and V3 cameras were updated to fix the vulnerability, the Wyze V1 camera was discontinued and is no longer receiving security patches. This left all customers who owned a Wyze V1 camera in a tough situation; either upgrade to the newest model, or remove the microSD card from their device and rely solely on cloud storage.
Eufy Camera Exploit – Remote Live Stream via RTSP
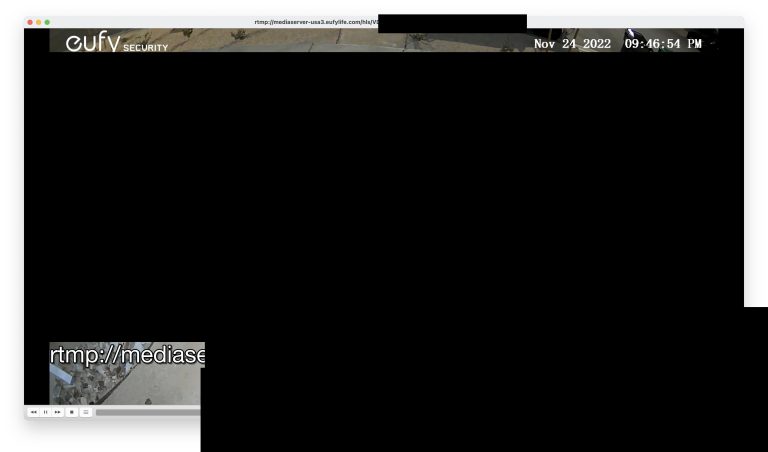
In November 2022, security researcher Paul Moore discovered a security vulnerability with Eufy cameras which allows an attacker to stream the cameras via VLC Media Player without any authentication or encryption.
This is a relatively easy vulnerability to exploit: You need the serial number of the camera and a four-digit random hex which can be brute forced with only 65,536 combinations. You can read TheVerge’s article for more information: Anker’s Eufy lied to us about the security of its security cameras.
Deceptive Advertising: Eufy Lied to Customers
Eufy’s advertising was built upon a promise of keeping customer’s data safe. Some of their claims include: “A guarantee that you have control over your own data” and “Protects you, your family, and your privacy”. As we can see now, these claims are entirely false and misleading.
I feel terrible for everyone who bought their products with a promise of security and privacy; only to find out they were lied to. This makes it harder for us to build trust in companies that may actually have a privacy-focused solution. Are they being honest, or are they just another Eufy?
Uniview Security “Exploits” – Accessing via VLC Media Player
One of the brands of security cameras we sell, Uniview, can also be accessed remotely via VLC Media Player. To prove a point, I’m going to show you how easy it is to view the cameras, and what you can do to make them secure.
To access a Uniview camera via VLC, you will need to understand the RTSP URL for the camera. Uniview’s RTSP URL is a string containing username, password, IP address, and port values. Together, this information is like a key that tells your computer where to find the camera stream, and how to unlock it.
Uniview’s RTSP URL follows this format:
rtsp://<username>:<password>@<ipaddress>:<port>/unicast/c<#>/s<#>/
- Username: The username for accessing the camera, typically “admin”
- Password: Set by the owner of the camera (9-32 characters, must include letters, digits, and special characters)
- IP Address: The external IP address of the camera’s network
- Port: The RTSP port of the camera (default 554)
- #: Channel number of the camera, and stream type (0 = main stream | 1 = sub stream)
As you can see, with just a few pieces of information you (or an attacker) are able to access a Uniview camera from anywhere in the world. However, this is not the same type of vulnerability as Eufy, as we’ll see in the next section.
Why Uniview is Secure (compared to Wyze and Eufy)
We just learned that Uniview cameras can be accessed over the internet via an RTSP URL, so what makes them more secure compared to Wyze and Eufy? Well, there are a few caveats to accessing the Uniview cameras.
First, you must forward your RTSP port to the internet. Without port forwarding, your cameras cannot be accessed via the RTSP stream.
This is not the case with Eufy. In Eufy’s case, information is being sent to Amazon’s cloud servers even without port forwarding. Attackers can view the stream with only the serial number and hex of Eufy’s cameras.
Second, Uniview cameras require a username and password for authentication. Without a password, you cannot access UNV cameras. This means you can make your cameras nearly impossible to access by choosing a strong password. The more difficult your password is to brute force, the more secure your cameras are.
Lastly, Uniview’s cameras can be run completely locally, without any internet access. For example, I can access my camera system at home by using the local IP address 192.168.0.5 of my Uniview recorder. As long as I don’t allow the unit to connect to the internet, it is impossible for anyone outside my local network to access the camera system.
Key Takeways and Final Thoughts
I was very frustrated to learn how large companies like Wyze and Eufy (owned by Anker) pretend to care about customer’s privacy, while simultaneously putting their customers in danger by refusing to fix vulnerabilities (Wyze) and denying any issues with their software (Eufy). These companies should be held legally responsible for their false advertising and negligence for keeping user’s information private.
I also find it frustrating to see how heavily these companies are recommended and advertised across the internet. When you Google “Best security cameras for home use”, you will find article after article promoting Eufy, Wyze, Arlo, Google Nest, and more similar products. These big tech companies have an advantage in marketing to consumers thanks to their use of Amazon affiliate links and large advertising budgets.
On the other hand, you will almost never come across an article recommending professional security camera brands such as Uniview, Hanwha, Bosch, or Axis. I suspect this is due to there being no monetary incentives to write an article about these products; as they are not sold through Amazon.
I hope you will remember which companies have been caught lying to their customers, and warn friends and family so they don’t make the same mistake. The more educated we are about the products we connect to our homes, the better decisions we can make for ourselves and the people in our lives.